The Progress Chef 360 platform delivers unprecedented improvements in performance, reliability and operational efficiency. In our latest update (Progress Chef 360 - 1.4), we have another set of powerful services that manage and enforce infrastructure consistency at scale with high availability.
The Chef Declarative State Management (DSM) service acts as a central repository for configuration data. It manages cookbooks, policies and metadata for nodes managed by Progress Chef Infra Client. DSM enables nodes to efficiently request and receive configuration details, enabling streamlined deployment and management processes.
Building on this foundation, DSM provides a range of operational and strategic benefits, making it a key feature of the Chef 360 platform. With DSM, you can gain the following benefits:
- Scalability:
The Chef 360 Platform Kubernetes-based runtime allows the DSM service to scale horizontally by adding or removing pods as needed. This is particularly valuable for enterprise environments with unpredictable workloads or rapid growth across global operations.
- High availability:
The DSM service on Kubernetes benefits from the platform’s self-healing capabilities, confirming services remain available even when unexpected failures occur. This is critical for enterprise operations that can’t tolerate downtime.
- Streamlined updates and rollbacks:
With DSM in the Chef 360 platform, updates are managed automatically and include preflight checks to maintain compatibility and increase upgrade success rates. You can roll back configuration changes and updates, reducing the risk of downtime or errors during upgrades. This is essential for enterprise change management processes.
- Resource optimization and cost efficiency:
The DSM service on Kubernetes can use dynamic resource allocation, maintaining efficient use of CPU, memory and storage, leading to cost efficiency.
Kubernetes allows the DSM service to operate within isolated containers, reducing attack surfaces while offering granular role-based access control. This is essential for enterprise security and compliance requirements.
Set Up Declarative State Management (DSM) with Your Existing Chef 360 Infrastructure
To set up the Chef 360 platform, please follow our guide.
The admin dashboard configuration page has a dedicated section for DSM.
Goto: https://<FQDN>:30000/secure-console
Config > Enable Declarative State Management (DSM) Service > Click on the Check box > Save Config > Submit›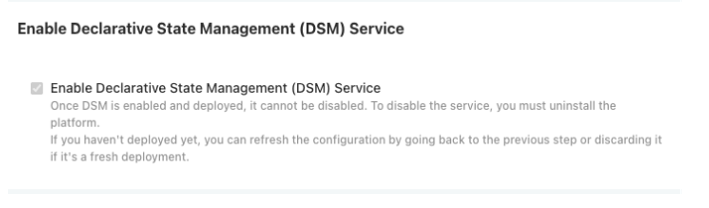
Note: Once DSM is enabled and deployed, it cannot be disabled. To disable the service, you must uninstall the platform.
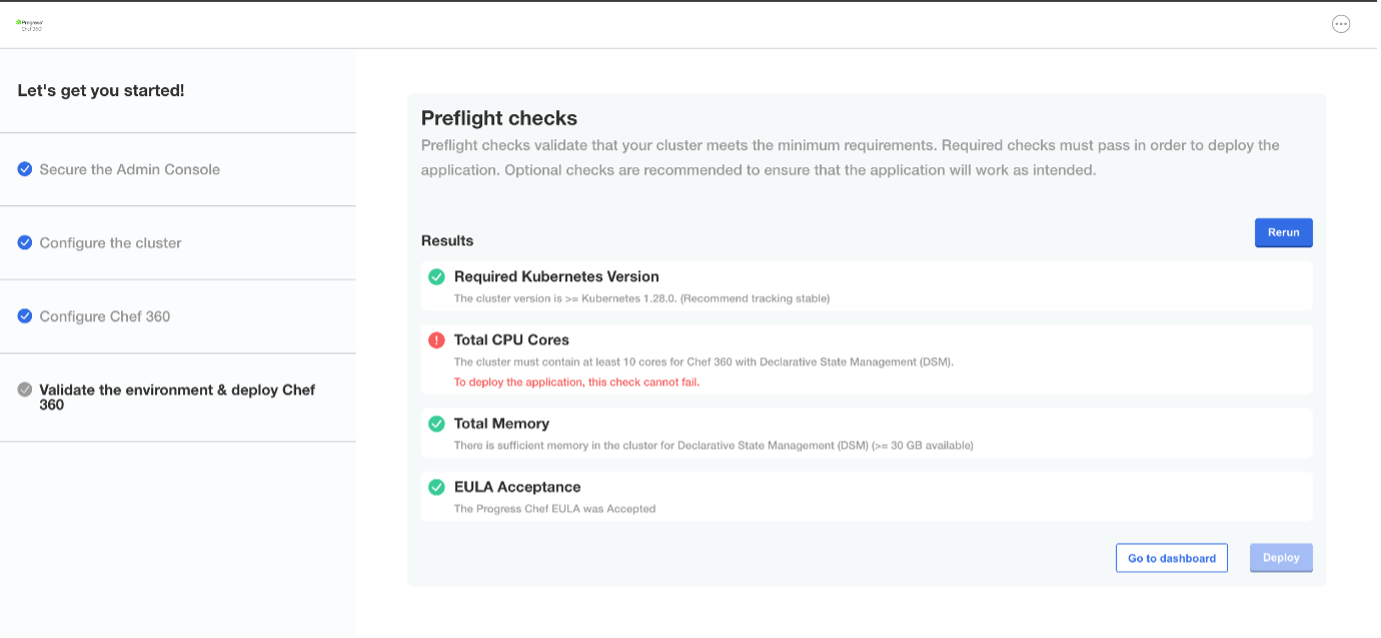
The cluster must contain at least 10 cores for Chef 360 with DSM or else the pre-flight checks will throw an error.
Configuration
Install Workstation:
The Chef Workstation is a toolset that provides everything you need to author, test and manage Chef automation code. It includes the Chef Infra Client, command-line tools like knife and testing frameworks, allowing you to develop and interact with your Chef infrastructure from your local machine.
To set up the Chef Workstation, please follow the steps given here.
Create an org: Org (short for organization) is a logical container used in Chef Server to group and manage Nodes (managed systems), Cookbooks, Roles, Environments, Users and Policies:
$ knife org create akshay “akshay-demo.pem” -a pivotal.
This newly created org will be added along with the FQDN:31000/organizations/<org> and now the knife is configured.
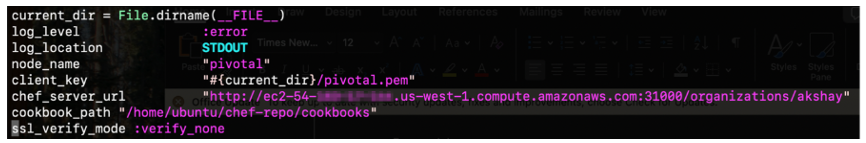
Navigate to ~/.chef directory and edit your config.rb or knife.rb file. Provide FQDN of your Chef 360 along with node_name, client_key and cookbook_path.
Create a new Chef repo to store your Chef content. It's also a good practice to initialize the directory with Git to be able to back up and share your content:
$ chef generate repo chef-repo
From the command line, run knife to fetch the SSL key, check it and confirm the configuration:
$ knife ssh fetch
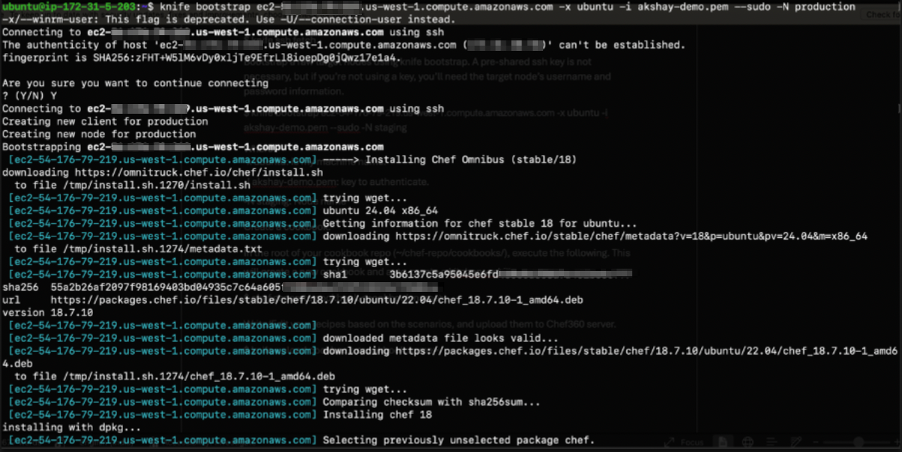
Bootstrap raw target nodes using knife bootstrap. A pre-shared SSH key is not necessary, but if you’re not using a key, you’ll need the target node’s username and password information.
$ knife bootstrap ec2-xx-xxx-xx-219.us-west-1.compute.amazonaws.com -x ubuntu -i akshay-demo.pem --sudo -N production
Where:
-x ubuntu: is the machine name.
-I akshay-demo.pem: key to authenticate.
-N production: Node name
Note: A target node is the server or machine you want to configure and manage using the Chef solution.
Create a cookbook:
In the root of your cookbook repo (~/chef-repo/cookbooks/), execute the following. This will create a new cookbook and auto-create a kitchen.yml file.
$ chef generate cookbook <cookbook name>
Write/Edit your recipes based on the scenarios and upload them to the Chef 360 server.
$ knife upload cookbook <cookbook name>
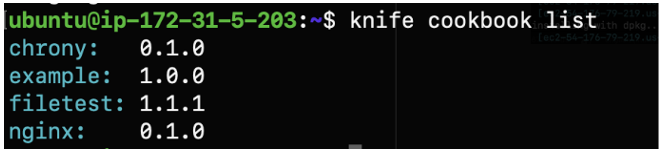
You can check the cookbook listing with the following command:
$ knife cookbook list
Once cookbooks are created and uploaded, you need to add them to the run-list associated with the nodes.
In this scenario, we are trying to install/update Chrony on an Ubuntu machine.
Chrony is a tool that keeps your computer’s clock accurate by syncing it with Internet time servers.
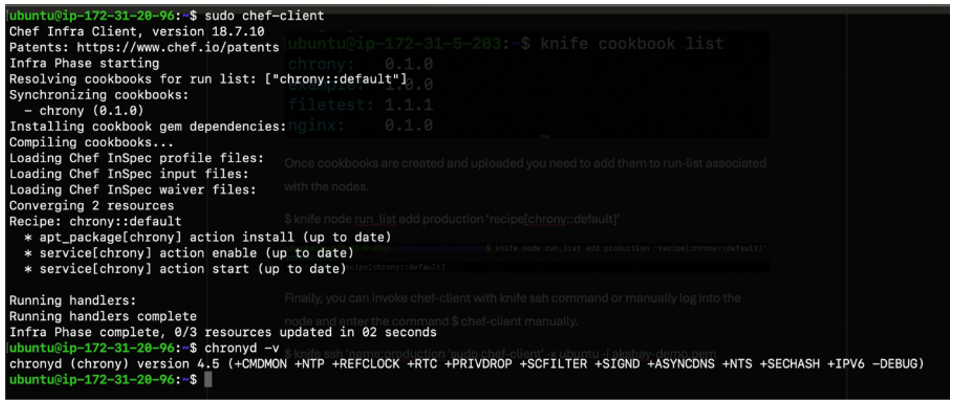
$ knife node run_list add production ‘recipe[chrony::default]’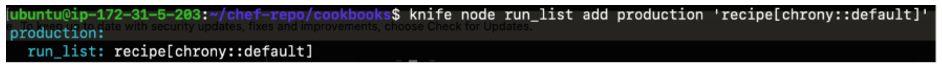
Finally, you can invoke chef-client with the knife ssh command or manually log into the node and enter the command $ chef-client manually.
$ knife ssh 'name:production 'sudo chef-client' -x ubuntu -i akshay-demo.pem
From the above screenshot and with the command $ chronyd –v we confirm Chrony is installed on the machine.
Conclusion
By adopting the new Chef 360 platform, you are preparing your infrastructure automation with a platform designed to evolve and integrate with emerging technologies.
For more information on Chef 360, visit us at chef.io. For more information about DSM, please visit the documentation page.
To try out the Chef 360 platform, request a trial today!